Although Chinese online shopping scams make up only 33% of all Chinese online frauds (source: https://www.statista.com/), while browsing the Internet with your eyes open and your credit card hopefully locked away, you seem to be constantly surrounded by fake web sites.
There are good educational sites explaining what online shopping scams are (like https://www.scamwatch.gov.au/) and how to detect them. There are also social media groups dedicated to warning the average consumer about fake online shops. Examples are „China Fake Shops! zB Zeitlosliebe WaldundFeld Fancyclothings Sonnesucht“ and „Who’s scamming you? Group“ on Facebook. Admins and people put a lot of effort into collecting and publishing information about fake online shops, but there is one problem: this will not make the problem go away!
While we can wait for politicians to address this issue with the Chinese government (will not happen) or for the postal fees from China to reach a level where making business directly from China does not make sense anymore, we can address the problem directly and shut the evil site down.
Now for several reasons this is almost always difficult. To shut down an online shop we need help from people who either already made money with the online shop (the web hosting service, the online shop platform like Shopify, the domain registrar, the certificate authority, and so on) or has limited interest in helping us (the providers of security trust certificates like Norton and McAfee).
There is one case where shutting down a fake online shop is possible: when the Chinese merchant counterfeit a big name such as Apple. Let´s look at such an example from this morning:
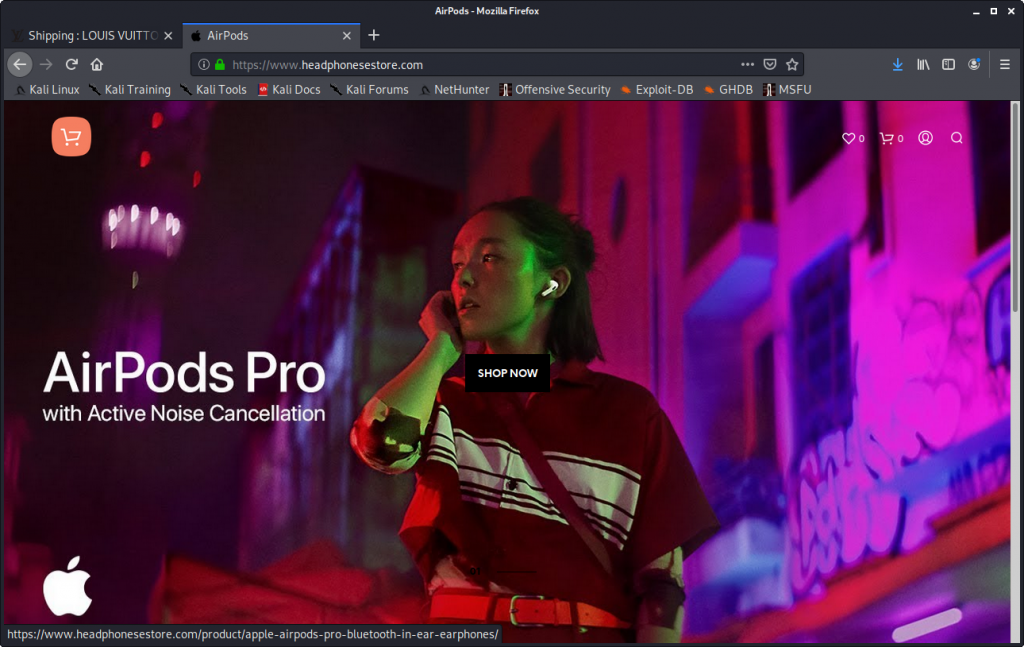
The online shop features many of the signs of typical Chinese scam sites: very cheap prices, a time limit on the sale, long shipping, no postal address, no return address, security trust certificates not real, spelling errors, a domain registration that is rather young, a TLS certificate registered just for some months, and customer reviews that look very suspicious.
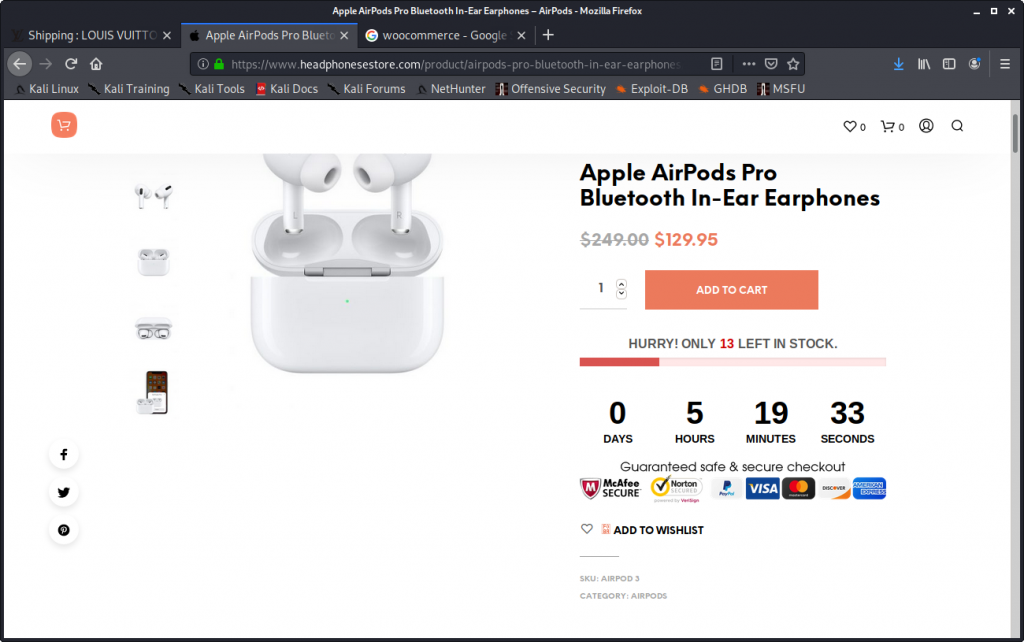
Please note the trust certificates („seals“) from companies McAfee and Norton (Broadcom) in above picture.
Apparently, the whole world thinks these products are just fantastic:
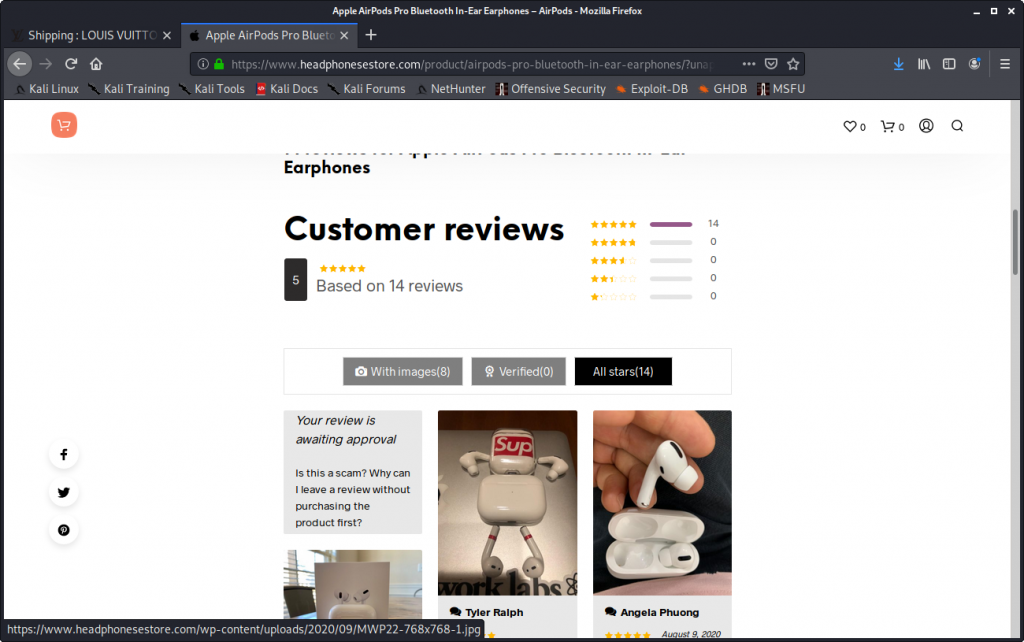
As the review page is badly coded, I could not resist to leave a „Scam site“ comment with an email return address of the Apple security team in Cupertino, CA:
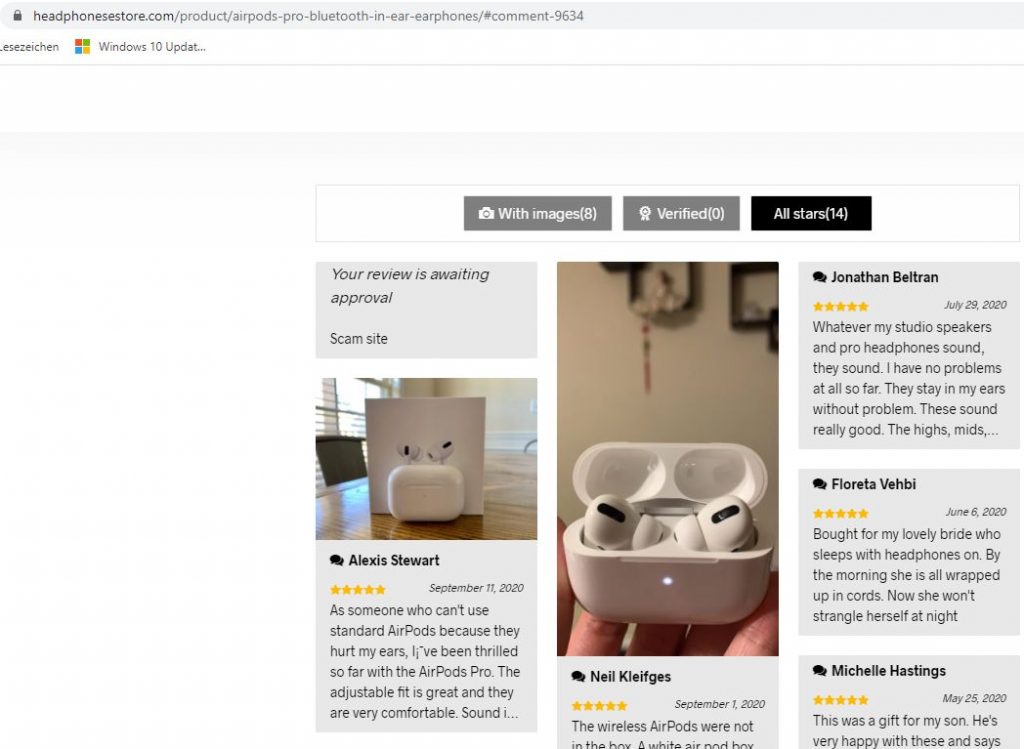
My „Scam site“ comment was visible until somebody in China must have woken up and removed it 🙂
Now comes success: Only a couple of hours later the online shop is down, erased from the Internet:
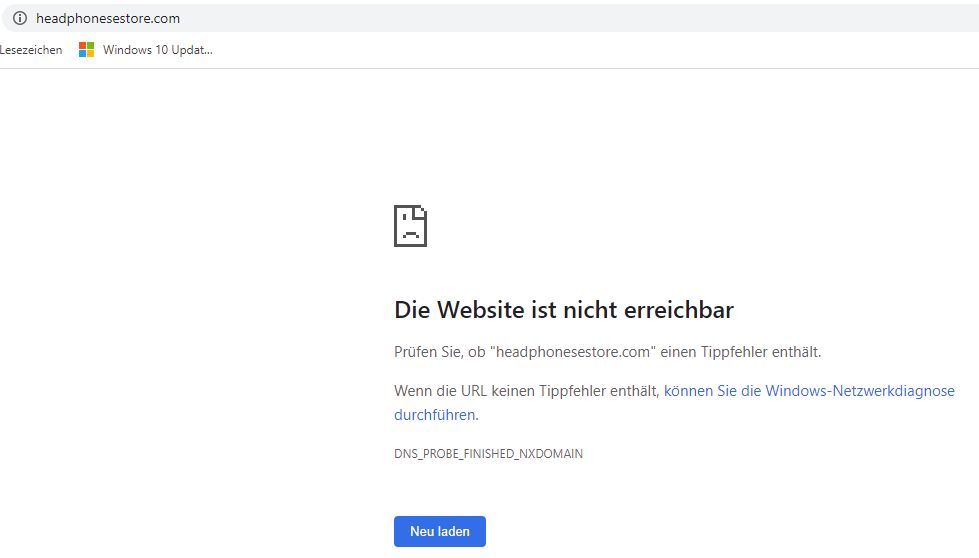
Technically speaking, the nameservers of the Internet now point to NS1.SUSPENDED-DOMAIN.COM and NS2.SUSPENDED-DOMAIN.COM when somebody tries to open up above online store, effectively directing traffic into the trash bin.
What had I to do today to make this happen?
- 0904 hours CET- I contacted the registrar of the domain name and made them aware of the shop. The registrar informs me immediately that sending an email is not enough and that I have to fill out a web form
- 0907 hours CET – After filling out the web form the registrar replies almost instantly with a case number (guys, your „noreply@salesforce.com“ sender address does not look very professional!)
- 0912 hours CET – After informing McAfee about illegal use of their trust certificate by email, they reply with a case number
- 0914 hours CET – Informed Norton about illegal use of their trust certificate by email. No answer
- 0919 hours CET – Informed Apple security team in the US by email about the fake shop. Automatic answer comes with case number
- 0923 hours CET – Informed the TLS certificate authority DigiCert about the use of one of their certificates for a fake shop
- 1246 hours CET – Domain registrar replies back that case is being worked on
As you can see, quite a lot of work goes into addressing just one online shopping scam site. Chinese scam gangs normally operate dozens of shops with different names.
Just a word of warning: Don´t do this at home. You have to be absolutely sure that you are not calling the wrong web site „fake“, unless you want to collect experience with the lawyers of angry companies. The above case is for educational purposes only, as operational information from such cases is not published on the Internet very often.
Above work has been done by me as a private person. No data nor resources from my workplace have been used.
Although the article is from 2010 and covers the PrestaShop free open-source E-commerce software, it describes very well what can happen to legit online shop owners if a Chinese gang takes over their business – even today: https://www.prestashop.com/forums/topic/46460-solvedsite-copied-and-hacked-by-chinese-company/. The mentioned Xin Net Technology Corporation is still doing its business and registered domains for scammers like uniqpek.com. From a PCWorld article: „From June 2008 through February, KnujOn said it found 34,283 illicit domains linked to Xin Net, covering unregulated prescription drugs, pirate software and counterfeit consumer goods.“. Now you probably understand why getting rid of one illicit online shop in China is not even the tip of the iceberg.